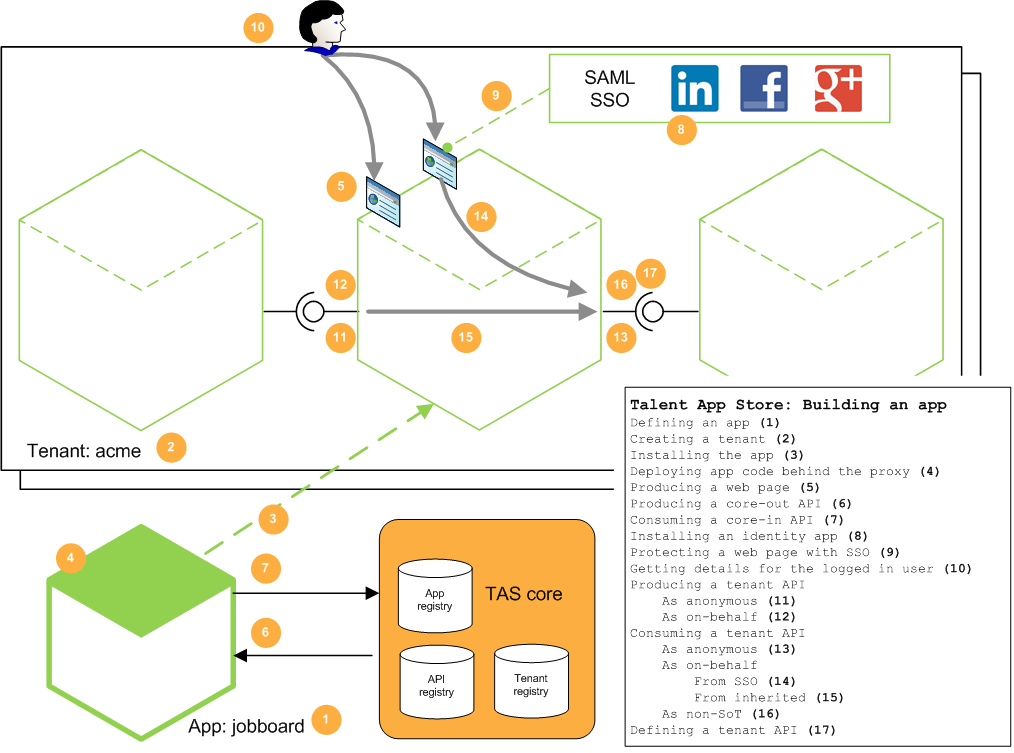
Connecting your app to Tazzy and the internet
You connect your app to the internet by placing it behind the Tazzy network proxy, a service provided by TAS.
To connect Tazzy to your app, you need to set the "Back end server" field for your app to point at your server's public internet address.
Traffic flows to/from your app
In most HR systems today, apps make API calls against the central system, not the other way around (and not from app to app).
In TAS, there is no central system. Any app can call an API on any other app. This peer to peer model means that, except for the simplest of apps, you'll need to mount API endpoints in your server, and allow inwards API traffic to them.
As well as incoming API traffic, your app may also support incoming SSO-protected traffic, as well as normal incoming traffic (i.e. nothing to do with TAS), so the overall picture is like this:
| incoming SSO traffic
|
| | normal incoming
| | web traffic
| |
| v
| +-------------------+
| |-------------------|
+---------------> || ||
|| ||
incoming API || ||
traffic || || outgoing API traffic
+---------------> || yourapp.com || +------------------+
| |-------------------| |
| +-------------------+ |
| |
| |
+-|----------------------------------------------------------|--+
| | v |
| |
| +--------+ +--------+ |
| |--------| +--------+ |--------| |
| || || |--------| || || |
| || || || || || || |
| |--------| || || |--------| |
| +--------+ |--------| +--------+ |
| +--------+ |
| |
| other installed apps + TAS core |
+---------------------------------------------------------------+
TAS uses the following industry standards for securing incoming and outgoing API and SSO traffic:
| Type of traffic | Security |
|---|---|
| Core APIs | HMAC |
| tenant APIs | OAuth |
| SSO | SAML 2 |
About Tazzy
Once your app is sitting behind Tazzy, all incoming API and SSO traffic passes through Tazzy, as does all outgoing API traffic.
Since Tazzy works at the network level, instead of libraries/SDKs, you can build your app in any language/framework.
Tazzy deals with:
- Service discovery
- API and SSO security
- Caching of e.g. OAuth tokens, and verifications
Once connected, the network paths look like this:
| incoming SSO traffic (https://communityapps.aotal.com/t/{tenant}/...)
|
| | normal incoming (https://yourapp.com/...)
| | web traffic
| +---+ | +---+
| | | v | |
| | | +-------------------+ | tazzy
| | | |-------------------| | |
+---------------> || || | |
| | || || | |
incoming API || || | |
traffic | || || | | outgoing API traffic
+---------------> || yourapp.com || +------------------+
| | | |-------------------| | | |
| | | +-------------------+ | | |
| | tazzy | | |
| | | | | |
| +---+ +---+ |
| back end server = e.g. |
| https://yourapp.com:8081/myapp |
| |
| |
+-|----------------------------------------------------------|--+
| | v |
| |
| +--------+ +--------+ |
| |--------| +--------+ |--------| |
| || || |--------| || || |
| || || || || || || |
| |--------| || || |--------| |
| +--------+ |--------| +--------+ |
| +--------+ |
| |
| other installed apps + TAS core |
+---------------------------------------------------------------+
Note: while developing your app, it can be convenient to run your server code on your personal machine and then use a tool like ngrok to expose it to the internet.
Securing your app's traffic to Tazzy
While Tazzy handles all HMAC, OAuth and SAML on behalf of your app, the path between your app and Tazzy should still be verified. To do this:
- Incoming traffic: Check that the incoming tazzy-secret request header matches the secret key of your app (you can find your app's secret key on the developer site), and reject all traffic that does not match.
- Outgoing traffic: Attach the tazzy-secret request header with the secret key of your app.
Hosting Tazzy yourself
In future Aotal plans to enable you to host the Tazzy system within your own network. For now, your app must use the community Tazzy, and the app settings pages in the developer site reflect this.
API paths